With data continuously growing in complexity and quantity, ensuring data security is more important than ever when choosing to buy a business intelligence (BI) solution.
From data protection to data governance, having a BI platform that enables you to control, audit, encrypt and manage user access and usage of sensitive data is essential.
What is equally important is whether a BI vendor offers the expected level of data security and compliance in their platform that adheres to international regulatory standards. Here are the 5 essential considerations for data security and compliance.
#1 - Secure Meta-Data Layer
Meta-data is what describes and provides information about every data object in a database. It gives necessary context about the data, underlying how what you see of the data in columns and rows. Think elements like when said data was uploaded, who uploaded it, the type of data, and so on, as well as components such as data formatting, calculated fields and table structures.
The meta-data layer sits between the user interface (UI) your users will use to build reports, and the queries they send to the database. Having a well-designed meta-data layer means you can support self-service analytics dashboards and queries with high performance and security.
The most secure BI vendors position their metadata layer as core to their data security offering. For example, Yellowfin implements its data security capabilities primarily at the metadata layer via several different components:
- Access Filters: Access filters are designed to restrict the availability of data based on the user running a report. It limits the dataset at the row-level, adding mandatory filters, and is only able to be changed by users with the appropriate security access level. Access filters define a user/row-level-value mapping, and then associate that mapping with the appropriate column in the metadata layer. For example, a manager might be only able to see staff details from reports within their own department.
- Column Level security: In most cases, a report or dashboard view is designed for general use, but the information within some columns may be highly sensitive and not intended for general consumption. Yellowfin offers the capability to secure columns individually to prevent and protect sensitive information from being queried in an ad-hoc report creation (i.e. self-service) capacity. This means only users with appropriate access can see the item/restricted columns when creating or viewing the report.
- Data Source Substitution: This is a multi-tenancy feature paired with client organizations that enables the ability to switch what data source a report is running against, based on what organization the user is in at the time the report is run. It is a helpful and protective data security feature useful if an organization separates their client data by databases with shared schemas, but only wants to create a single report.
Because meta-data typically offers administrative, descriptive and structural information around data elements, which help you query and explore large amounts of data faster, the challenge is in ensuring these descriptive elements are equally as secure as what is stored within each object. This makes a secure meta-data layer one of the most essential data security considerations.
Learn More: Yellowfin Technical Architecture - The Meta-Data Layer
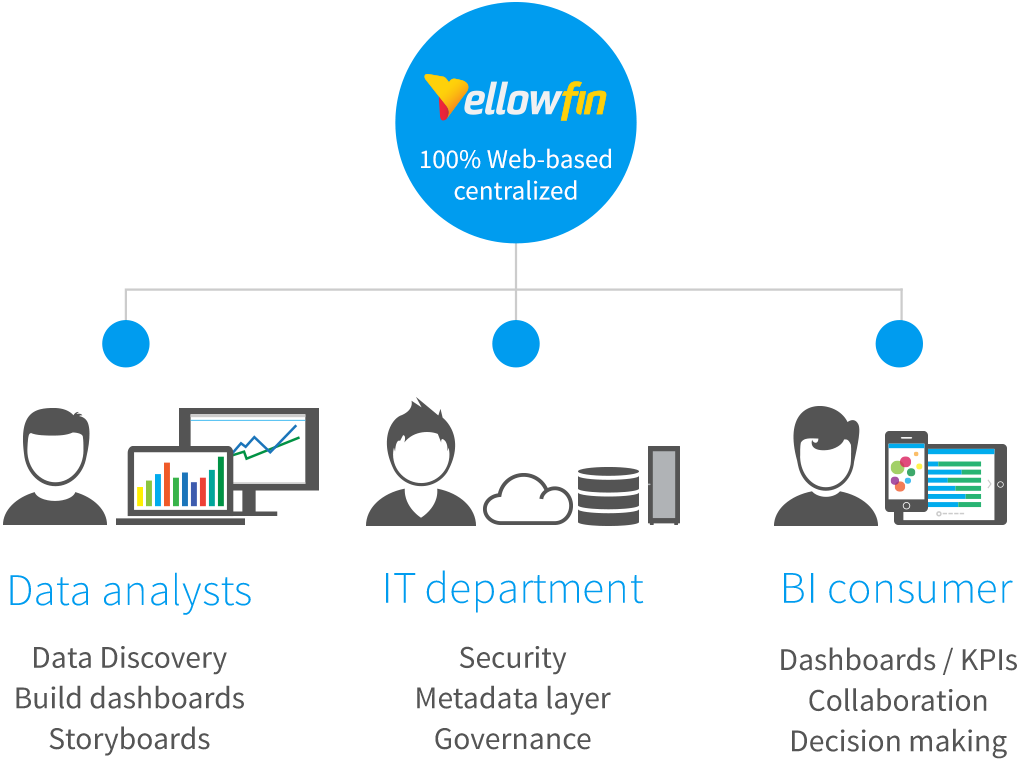
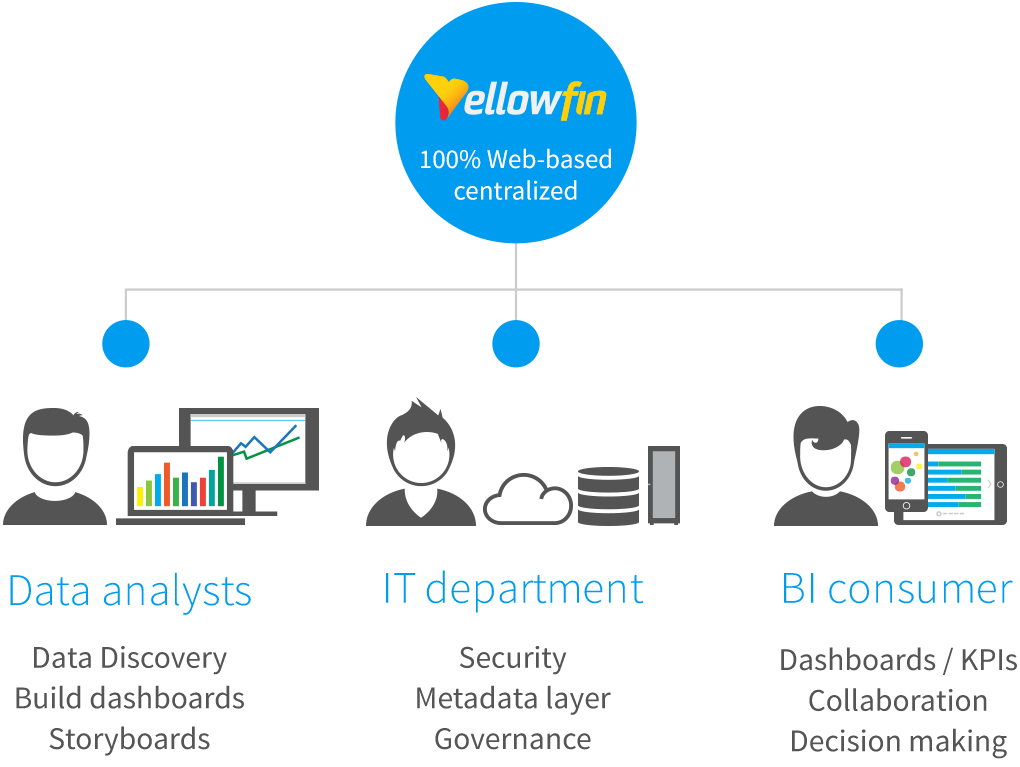
#2 - Role-based Access Control (RBAC)
Role-based access controls and authentication is an important modern capability that every analytics solution should provide. A role is essentially a collection of available security functions, which each intended analytics user is associated with to manage their available system functions within the application (report creation, data story authoring, etc), as well as links and permissions over what data is made available for reporting.
Having role-based access in an analytics solution allows for clearly defined control over what data is able to be accessed and shared based on users’ needs, departments, etc.
For example, you may have a group of BI users who only need to view reports your team creates for them; in this case, their role may limit their functionality to read-only capacity.
Another example would be assigning a specific group of BI users access to certain AI-powered features (not to be confused with AI capabilities of non-analytics tools such as ChatGPT) of the analytics platform in question, such as Yellowfin Guided NLQ.
Yellowfin provides both pre-built roles and the ability to create your own roles and assign whatever system functions are required for that specific role, helping enterprise and smaller organizations enforce fine-grained access controls over their most critical and sensitive content. Roles and other user attributes can be modified programmatically using Yellowfin’s extensive administration controls.
Meanwhile, having the ability to synchronize each user’s attributes and security access is an integral step of a standard SSO implementation, which is the next major consideration.
Learn More: Yellowfin Security Model - Functional, Content and Data Security
#3 - Single-Sign On (SSO)
Single sign-on (SSO) is an authentication capability that allows users to log in different applications and websites using a common ID. It’s an increasingly important security measure, and it’s just as important your chosen BI vendor supports this authentication method, so your analytics users can access their BI tools securely and seamlessly.
Modern SSO is generally expected to provide the capabilities and granularity to control the session state for users’ interactions with the analytics suite, as well as the ability to manage session times and/or terminate sessions, with, at minimum, a global setting for single lockout and session management. This is in addition to supporting other user authentication methods, such as Security Assertion Markup Language (SAML) and Multi-Factor Authentication (MFA), both of which make secure connections and the secure transfer of identity data between two entities (the identify provider used (such as Okta) and the service provider (your analytics suite).
Yellowfin allows for integration with all third-party authentication processes mentioned above. Its SSO implementation is based on a model of user replication, which ensures every Yellowfin user only has access to what the admin wants them to via synchronization of the user’s role (which governs content access and available system functions) and their authentication services. An custom authentication bridge is used when connecting Yellowfin with a third party authentication process, matching it with the user’s credentials/attributes in the Yellowfin system for airtight security. Once the match is made, the bridge will execute a SSO of that user into Yellowfin.
Yellowfin also allows for a prebuilt SAML Bridge for SSO (for organizations that use identity access providers like ADFS or Okta) which allow for even more seamless configuration for user authentication. These are just some of the options available; you can read more in the link below.
Learn more: Single-Sign On in Yellowfin - How Does It Work?
#4 - Content Security
Content management within an analytics suite is one of the most important capabilities organizations need to look for in an analytics solution. The ability to customize, limit and control who can access content by what delineation (department, project, etc) or experience (general reports, day-to-day summaries, management reports, etc) is key to ensuring the right permissions are enforced, and that tailoring complex and granular user experiences that also keeps sensitive data safe and secure are possible.
In Yellowfin, content security and management is a large part of its data governance and data security capabilities. Yellowfin organizes and secures data by placing it into a structure known as Content Folders, which delineate content by business unit and modularize content by needs. Each individual content or its folder can be layered with unique user permissioning. Content security ties into Yellowfin’s role-based access controls, where a user is assigned access to content folders and the items based on their current role permissions, group membership, or on an individual basis.
Learn More: Yellowfin Content Security
#5 - SOC Assessment and GDPR Approved
Data compliance goes hand in hand with data security and data governance. If a BI vendor doesn’t have the necessary external accreditations, or doesn’t follow important standards surrounding the encryption, storage, access and protection of sensitive customer data, it’s only a matter of time before you might face an unintentional or malicious data breach - and fines.
Yellowfin takes data security and compliance very seriously, achieving a Service Organization Control for Service Organizations (SOC 2) Type II certification in 2021 to provide the highest standards of quality across international compliance, regulations and security for all customers and their data. SOC reports provide assurance over control environments as they relate to the retrieval, storage, processing, and transfer of data, complying with industry expectations and regulations around operating a secure and compliant company at all levels.
In addition, Yellowfin is compliant with General Data Protection Regulation (GDPR), HiPPA, PCI and UK Cyber Essential regulatory standards, of which you can learn more in the link below.
Learn More: Yellowfin’s Security & Compliance - All Accreditations
Yellowfin BI: End-to-End Data Security
Learn more about Yellowfin’s comprehensive data security and data governance capabilities, along with its embedded analytics suite with a free demo - or speak to our sales team members today for more information.